initial commit
This commit is contained in:
commit
af67b7de53
17
README.md
Normal file
17
README.md
Normal file
|
|
@ -0,0 +1,17 @@
|
||||||
|
# @BayernWLAN login with ESP
|
||||||
|
|
||||||
|
This repository contains two example how to log in to the captive portal of `@BayernWLAN` wifi networks using an ESP.
|
||||||
|
|
||||||
|
Normally after connecting to the network you would click the connect button in the captive portal of your browser to get access to the internet.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Of course this is difficult to do with the ESP since you have neither a web browser with a graphical interface, nor a mouse to click any buttons.
|
||||||
|
|
||||||
|
Instead, we can emulate the click on the button by sending a specific `HTTP GET` request to the access point.
|
||||||
|
|
||||||
|
There is [one example][micropython-example] for use with MicroPython and a [second example][arduino-example] for the Arduino IDEBoards Manager.
|
||||||
|
The arduino code uses the libraries `HTTPClient.h` and `WiFi.h` which should be built-in.
|
||||||
|
|
||||||
|
[micropython-example]: example_micropython.py
|
||||||
|
[arduino-example]: example_arduino.ino
|
||||||
79
example_arduino.ino
Normal file
79
example_arduino.ino
Normal file
|
|
@ -0,0 +1,79 @@
|
||||||
|
/*
|
||||||
|
* Example of how to log in to captive portal of @BayernWLAN with an
|
||||||
|
* ESP32
|
||||||
|
*
|
||||||
|
* The program connect to the @BayernWLAN wifi and sends a HTTP request
|
||||||
|
* that emulates the click on the Connect button in the captive portal.
|
||||||
|
*
|
||||||
|
*/
|
||||||
|
|
||||||
|
#include <WiFi.h>
|
||||||
|
#include <HTTPClient.h>
|
||||||
|
|
||||||
|
const char* ssid = "@BayernWLAN"; //Enter SSID
|
||||||
|
const char* password = "";
|
||||||
|
|
||||||
|
// root certificate for the vodafone hotspot
|
||||||
|
const char* root_ca= \
|
||||||
|
"-----BEGIN CERTIFICATE-----\n"
|
||||||
|
"MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh\n"
|
||||||
|
"MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3\n"
|
||||||
|
"d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD\n"
|
||||||
|
"QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT\n"
|
||||||
|
"MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j\n"
|
||||||
|
"b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IENBMIIBIjANBgkqhkiG\n"
|
||||||
|
"9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4jvhEXLeqKTTo1eqUKKPC3eQyaKl7hLOllsB\n"
|
||||||
|
"CSDMAZOnTjC3U/dDxGkAV53ijSLdhwZAAIEJzs4bg7/fzTtxRuLWZscFs3YnFo97\n"
|
||||||
|
"nh6Vfe63SKMI2tavegw5BmV/Sl0fvBf4q77uKNd0f3p4mVmFaG5cIzJLv07A6Fpt\n"
|
||||||
|
"43C/dxC//AH2hdmoRBBYMql1GNXRor5H4idq9Joz+EkIYIvUX7Q6hL+hqkpMfT7P\n"
|
||||||
|
"T19sdl6gSzeRntwi5m3OFBqOasv+zbMUZBfHWymeMr/y7vrTC0LUq7dBMtoM1O/4\n"
|
||||||
|
"gdW7jVg/tRvoSSiicNoxBN33shbyTApOB6jtSj1etX+jkMOvJwIDAQABo2MwYTAO\n"
|
||||||
|
"BgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUA95QNVbR\n"
|
||||||
|
"TLtm8KPiGxvDl7I90VUwHwYDVR0jBBgwFoAUA95QNVbRTLtm8KPiGxvDl7I90VUw\n"
|
||||||
|
"DQYJKoZIhvcNAQEFBQADggEBAMucN6pIExIK+t1EnE9SsPTfrgT1eXkIoyQY/Esr\n"
|
||||||
|
"hMAtudXH/vTBH1jLuG2cenTnmCmrEbXjcKChzUyImZOMkXDiqw8cvpOp/2PV5Adg\n"
|
||||||
|
"06O/nVsJ8dWO41P0jmP6P6fbtGbfYmbW0W5BjfIttep3Sp+dWOIrWcBAI+0tKIJF\n"
|
||||||
|
"PnlUkiaY4IBIqDfv8NZ5YBberOgOzW6sRBc4L0na4UU+Krk2U886UAb3LujEV0ls\n"
|
||||||
|
"YSEY1QSteDwsOoBrp+uvFRTp2InBuThs4pFsiv9kuXclVzDAGySj4dzp30d8tbQk\n"
|
||||||
|
"CAUw7C29C79Fv1C5qfPrmAESrciIxpg0X40KPMbp1ZWVbd4=\n"
|
||||||
|
"-----END CERTIFICATE-----\n";
|
||||||
|
|
||||||
|
void setup() {
|
||||||
|
Serial.begin(115200);
|
||||||
|
|
||||||
|
// Connect to wifi
|
||||||
|
WiFi.begin(ssid, password);
|
||||||
|
|
||||||
|
// Wait some time to connect to wifi
|
||||||
|
for(int i = 0; i < 10 && WiFi.status() != WL_CONNECTED; i++) {
|
||||||
|
Serial.print(".");
|
||||||
|
delay(1000);
|
||||||
|
}
|
||||||
|
Serial.println("WiFi connected!");
|
||||||
|
|
||||||
|
// Send HTTP request for login
|
||||||
|
HTTPClient http;
|
||||||
|
http.begin("hotspot.vodafone.de", 443, "/api/v4/login?loginProfile=6", root_ca);
|
||||||
|
String payload = String("Accept: */*\r\n\r\n");
|
||||||
|
size_t payload_size = payload.length();
|
||||||
|
int httpCode = http.sendRequest("GET", (uint8_t *) payload.c_str(), payload_size);
|
||||||
|
|
||||||
|
if (httpCode > 0) { //Check for the returning code
|
||||||
|
String payload = http.getString();
|
||||||
|
Serial.println(httpCode);
|
||||||
|
Serial.println(payload);
|
||||||
|
}
|
||||||
|
else {
|
||||||
|
Serial.println("Error on HTTP request");
|
||||||
|
Serial.println(httpCode);
|
||||||
|
}
|
||||||
|
|
||||||
|
http.end();
|
||||||
|
|
||||||
|
Serial.println("IP address: ");
|
||||||
|
Serial.println(WiFi.localIP());
|
||||||
|
}
|
||||||
|
|
||||||
|
void loop() {
|
||||||
|
|
||||||
|
}
|
||||||
36
example_micropython.py
Normal file
36
example_micropython.py
Normal file
|
|
@ -0,0 +1,36 @@
|
||||||
|
import network
|
||||||
|
import ussl
|
||||||
|
import socket
|
||||||
|
import time
|
||||||
|
|
||||||
|
def sock(host, port, ssl = False):
|
||||||
|
s = socket.socket()
|
||||||
|
ai = socket.getaddrinfo(host, port)
|
||||||
|
addr = ai[0][-1]
|
||||||
|
s.connect(addr)
|
||||||
|
if ssl:
|
||||||
|
return ussl.wrap_socket(s)
|
||||||
|
else:
|
||||||
|
return s
|
||||||
|
|
||||||
|
def http_get(sock, host, path):
|
||||||
|
sock.write(("GET " + path + " HTTP/1.1\r\nHost: " + host + "\r\nUser-Agent: curl/7.60.0\r\nAccept: */*\r\n\r\n").encode('utf-8'))
|
||||||
|
return sock
|
||||||
|
|
||||||
|
def connect_wlan(timeout = None):
|
||||||
|
wlan = network.WLAN(network.STA_IF)
|
||||||
|
wlan.active(True)
|
||||||
|
if not wlan.isconnected():
|
||||||
|
start = time.ticks_ms()
|
||||||
|
wlan.connect('@BayernWLAN')
|
||||||
|
while wlan.status() != network.STAT_GOT_IP and (not timeout or time.ticks_diff(time.ticks_ms(), start) < timeout):
|
||||||
|
time.sleep_ms(100)
|
||||||
|
return wlan.status()
|
||||||
|
|
||||||
|
def login_wlan():
|
||||||
|
s = sock("hotspot.vodafone.de", 443, True)
|
||||||
|
http_get(s, "hotspot.vodafone.de", "/api/v4/login?loginProfile=6")
|
||||||
|
return s
|
||||||
|
|
||||||
|
connect_wlan()
|
||||||
|
login_wlan().read(32)
|
||||||
BIN
images/captive-portal.png
Normal file
BIN
images/captive-portal.png
Normal file
Binary file not shown.
|
After 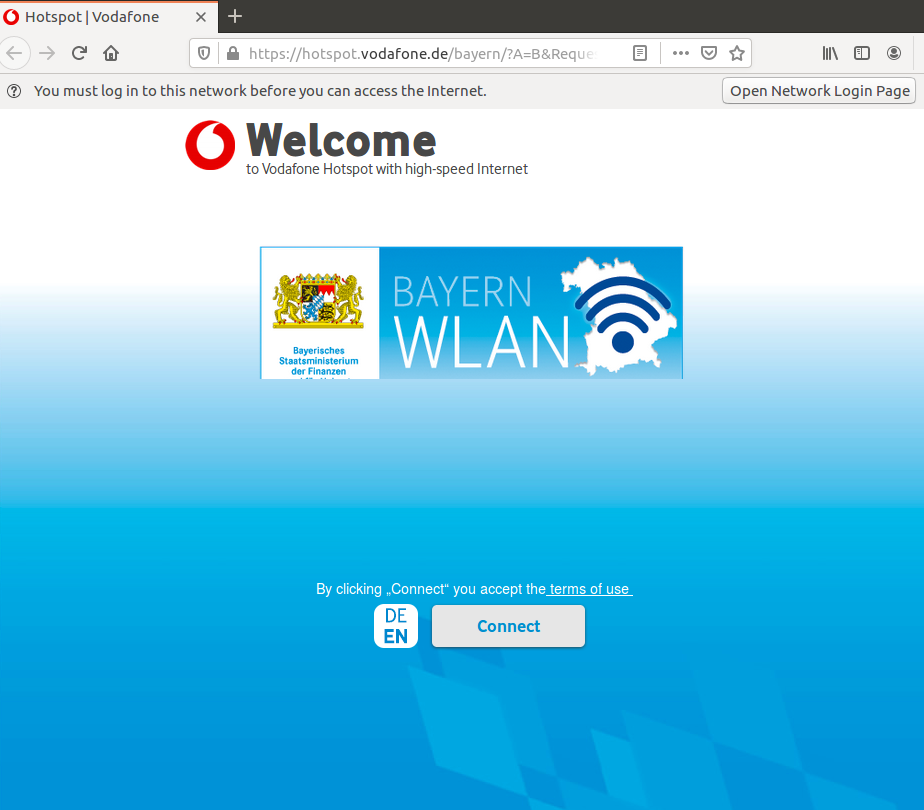
(image error) Size: 118 KiB |
Loading…
Reference in New Issue
Block a user